Make your door smart
Turn your smartphone into a key and transform the way you come home. With our most advanced retrofit solution, the Nuki Smart Lock Pro.
Buy now
All about Nuki
Top rated Nuki app
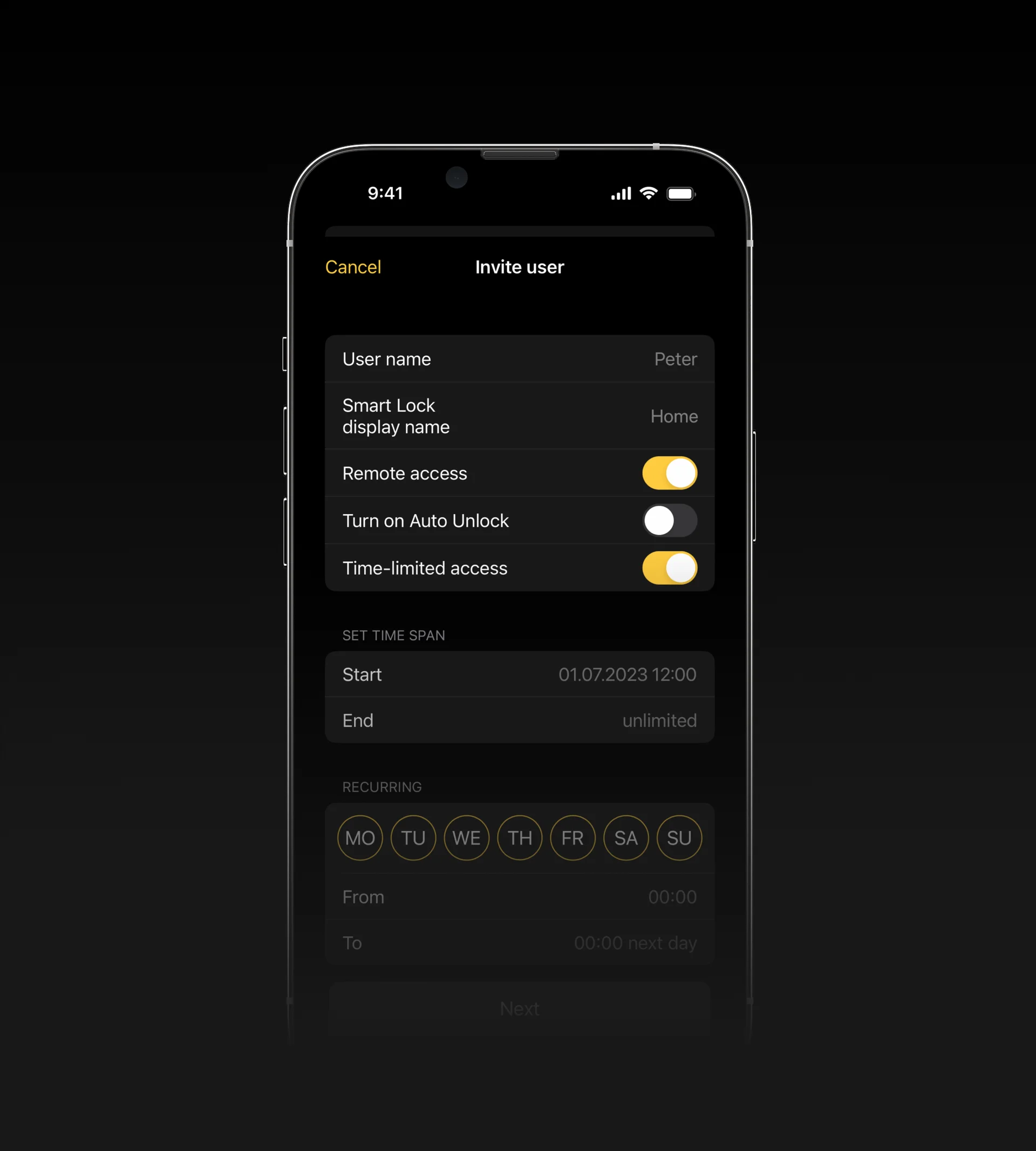
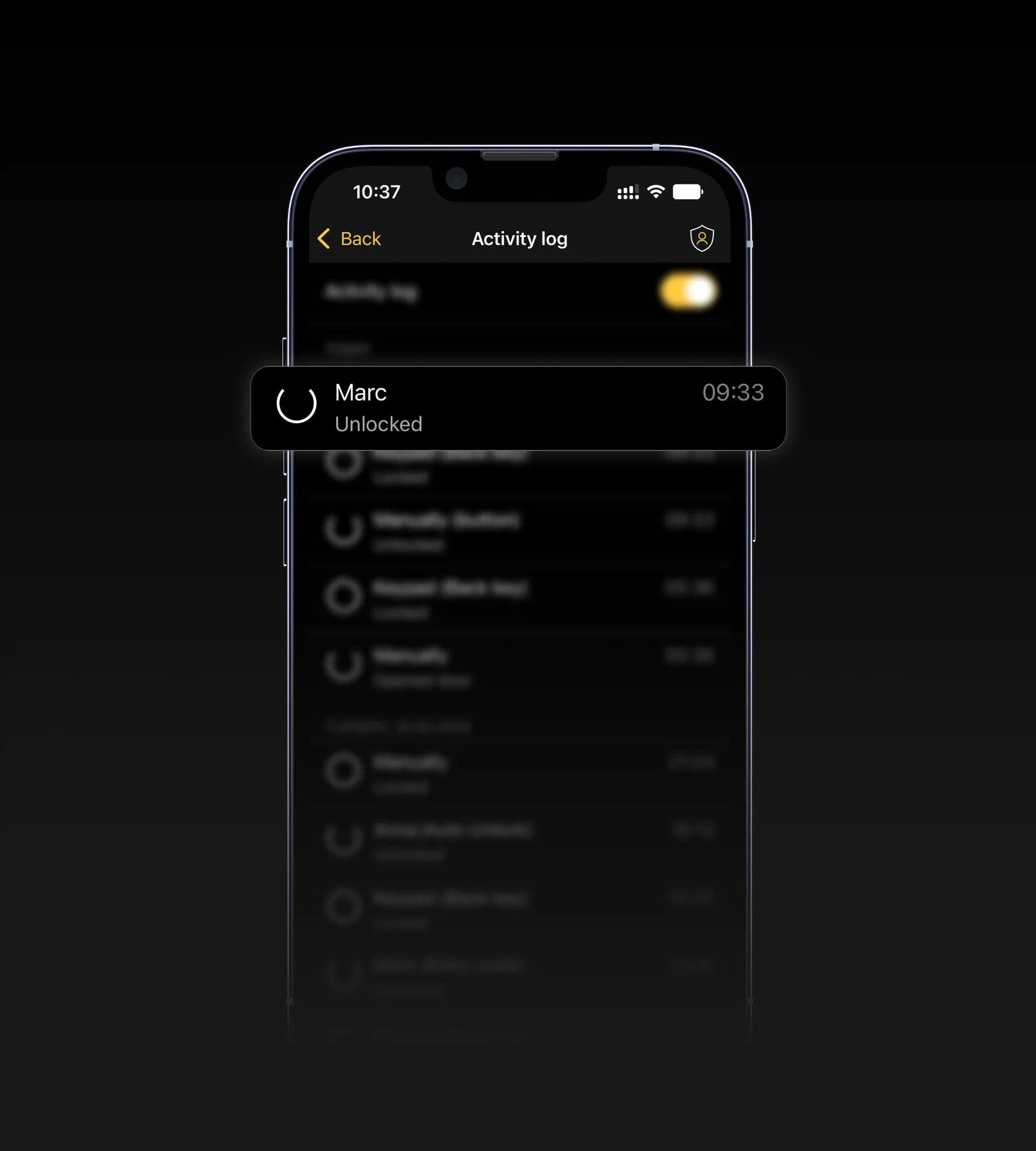
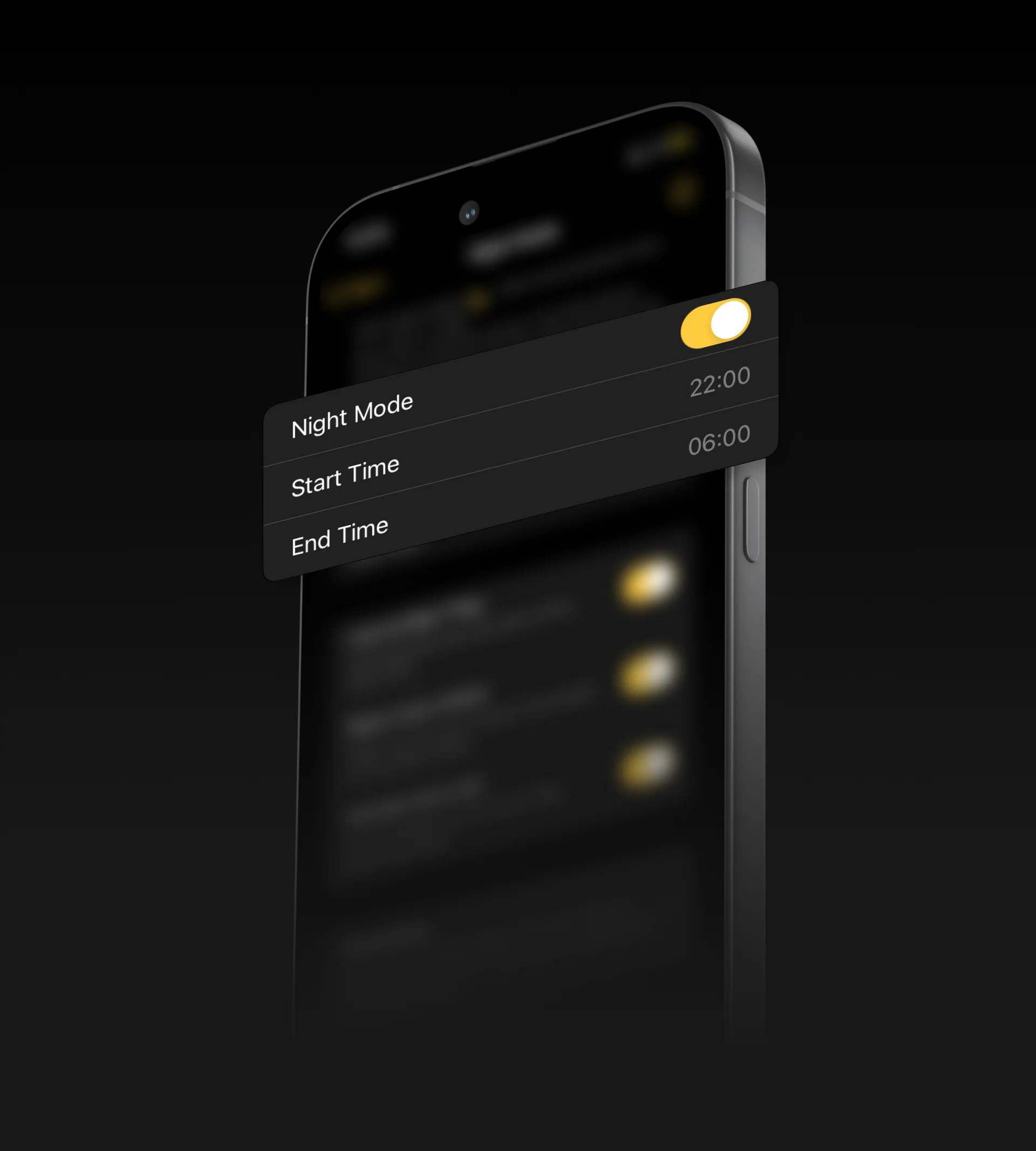
Do everything and more. No matter your schedule, Nuki adapts to it.
The New Smart Lock Generation – Presented by Nuki’s Founders

Join the Nuki Club.
Discover exclusive and personalized offers, insider news and many other benefits.
Discover all our products

Endless ways to open - smart accessories and features
Want to leave your phone at home? Nuki offers multiple options for opening your door: with fingerprints, codes, a Fob, your smartwatch or even your physical keys.
Discover products

Designed in Austria - made in Europe
Nuki products are made to last. Both our hardware and software are developed by teams of experts in Europe and uphold the highest production and privacy standards.