
Focused on security: Nuki’s encryption concept – explained simply
Stay SecureProtecting one’s home is one of the most basic human needs. We all want to be able to feel safe and secure within our own four walls. With the advance of digitization, issues like data protection and data security are also becoming increasingly important. As makers of electronic door locks we’re often asked to address our customers’ concerns: How secure is Nuki? Can the Nuki Smart Lock be hacked? What if I lose my smartphone? Does Nuki record my personal information somewhere?
The importance of security at Nuki
Anyone who has known Nuki from the start also knows just how serious we are about security. When we use the terms SMART, SIMPLE, and SECURE to describe the Nuki (“new key”) brand, we really mean it. To guarantee the safety of our products, we work with independent security institutes such as AV-TEST. We successfully completed the AV-Test process in both 2018 and 2019 in order to have the Nuki Combo and the Nuki Opener certified as “Secure Smart Home Products”. One thing that stood out in particular, was the Nuki encryption concept. This blog post will explain how our encryption concept works in a way that’s easy to understand.
Bluetooth as a communication standard
The Nuki Smart Lock uses Bluetooth Low Energy (BLE) in order to communicate with the Nuki app. The current Bluetooth standard (BLE 5) is remarkably energy-efficient and has excellent range. For security reasons, we have created our own encryption protocol to use alongside normal Bluetooth communication.
End-to-end encryption
Communication between the Nuki app and the Nuki Smart Lock uses a unique key that is known only to the two devices. In order to protect against attackers, the data is encrypted before it is transmitted (from say, the Nuki app). This is done using a NaCl (Networking and Cryptography library) procedure, which uses one-time, unique combinations of letters and numbers. This encrypted data is transmitted via Bluetooth and decrypted by the receiver (in this case the Nuki Smart Lock).
Simplified example:
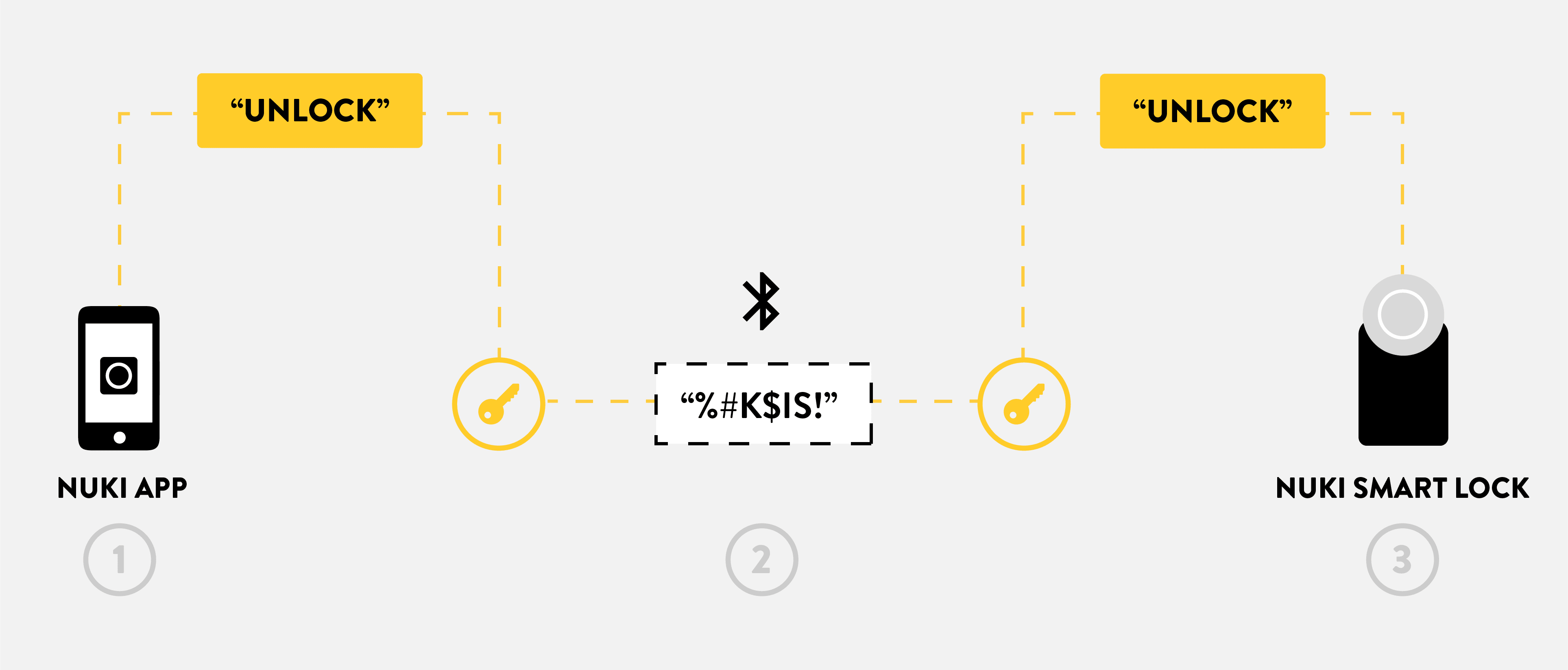
The Nuki app sends the “Unlock” command, encrypting it in such a way that the key is known only to the app itself and to the Nuki Smart Lock.
The Nuki app transmits the encrypted message to the Nuki Smart Lock via Bluetooth.
The Nuki Smart Lock recognises the key and is thus able to decrypt the incoming message and carry out the “Unlock” command.
Encryption when using Nuki Bridge
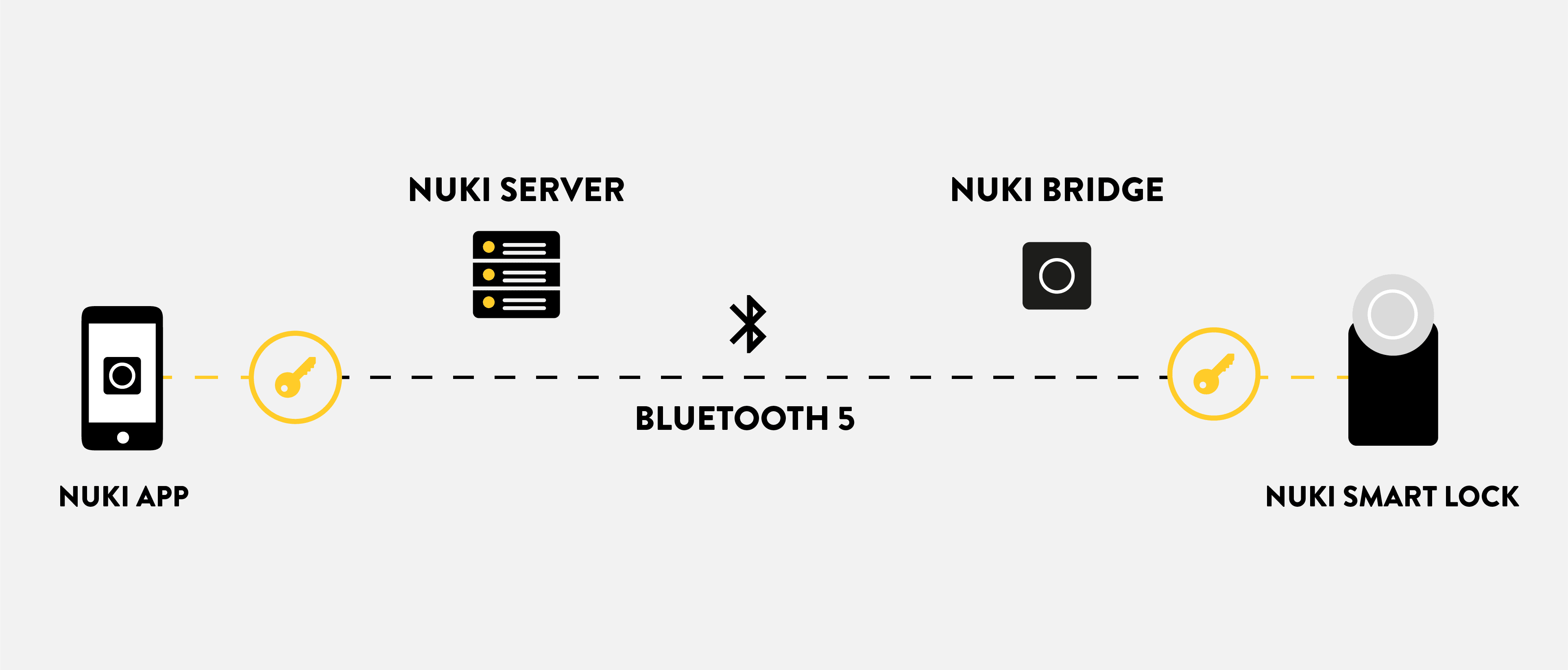
In order to check the status of your door lock remotely using the protocol in the Nuki app, you need to use the Nuki Bridge. This device is plugged into an outlet near the Smart Lock and connected to your home’s own Wi-Fi system, permanently connecting it to our Nuki servers.
It goes without saying that all data sent to your Nuki Smart Lock to or from the Nuki Bridge is also encrypted, using the same key known only to your Nuki app and to your Smart Lock. This key is otherwise unable to be deciphered in transit, either by the Bridge or the Nuki server. This means that we are unable to read the data, which also means we don’t save any information on our servers regarding the communication between the Nuki app and the Nuki Smart Lock.
Exchanging and saving keys
The Nuki app and the Nuki Smart Lock encrypt the commands sent between them. In order to ensure that the shared key is only visible to the two devices, a key exchange takes place. This “Diffie-Hellman key exchange” is carried out during the pairing process between the app and the Smart Lock. The private key is created without ever being transmitted from one device to the other. This is done using public and private keys. These randomly generated variables are then used to create a shared key.
These keys are stored on the smartphone and cannot be accessed by either the user or other apps. If you lose your smartphone, you can delete the permission from the Smart Lock. Doing so requires another smartphone with the proper permissions. Alternatively, you can perform a factory reset on the Nuki Smart Lock.
Challenge-response procedure
Suppose an attacker wanted to hack into a stranger’s home by recording the “Unlock” command in order to trigger the unlock process himself. These kinds of criminal “replay” attacks are prevented by our challenge-response procedure. A large random number is sent to the Nuki app via the encrypted channel (“Challenge”). This number must then be given by the Nuki Smart Lock in its reply (“Response”). If the number is incorrect or no number at all is transmitted, the command is rejected.
Simplified example:
The Nuki app receives a random number during the “Unlock” process. The “Unlock” command cannot be sent to the Nuki Smart Lock unless it includes the exact same random number. If another “Unlock” command with the same random number is then sent to the door lock, the command will be rejected by the Nuki Smart Lock.
Let’s conclude by summing up the most important details:
Security is a very important issue for Nuki. This is why we regularly have our products vetted and certified by external security institutions. In addition to normal Bluetooth communication, we have created our own encryption protocol for security reasons. Nuki uses the end-to-end encryption concept similar to what is used in online banking. Data is kept secure and well-protected when using the Nuki Bridge as well. The challenge-response procedure makes it possible to successfully fend off hacker attacks. If no random number is transmitted, or the wrong random number is sent, the “Unlock” command (for example) is rejected.




